Quantum entanglement makes quantum communication even more secure!
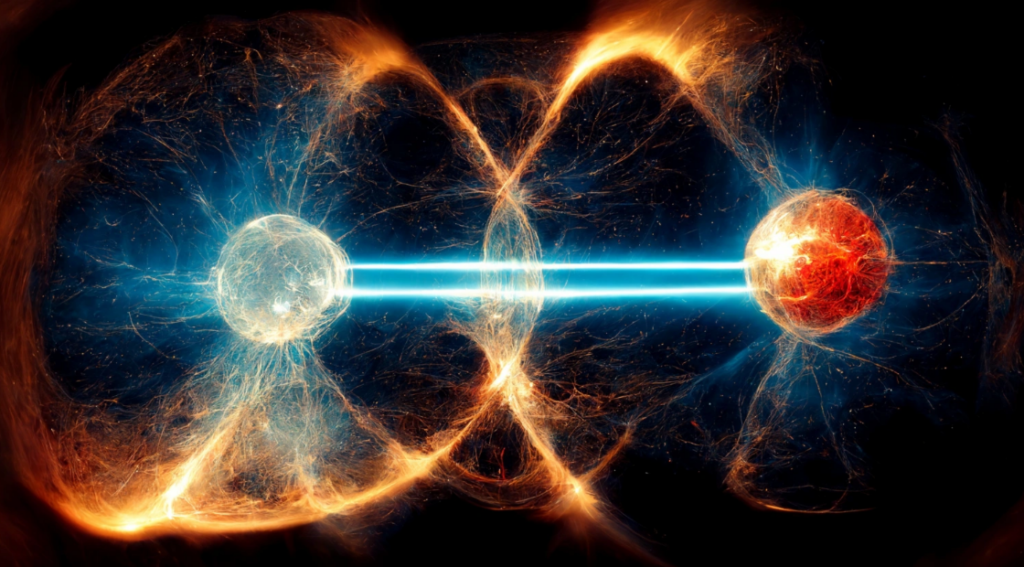
Stealthy communication is now more secure thanks to quantum entanglement. Quantum physics provides a way to share secret information that is mathematically proven to be safe from the prying eyes of spies, but until now, demonstrations of the technique, called quantum key sharing, have been based on one assumption: You must knowing that the devices used to create and measure quantum particles are flawless. Hidden flaws could allow a stealthy intruder to penetrate security without being noticed.
Now three teams of researchers have demonstrated the ability to perform secure quantum communications without prior confirmation that the devices are effective. The method, called device-independent quantum key distribution, is based on quantum entanglement, a mysterious relationship between particles that links their properties even when they are separated by long distances. In everyday communication, such as transmitting credit card numbers over the Internet, a secret code or key is used to distort the information so that it can only be read by someone else with the key. But there’s a dilemma: how can a distant sender and receiver share that key while making sure no one else has intercepted it along the way?


Quantum physics provides a way to share keys by transmitting a series of quantum particles, such as particles of light called photons, and making measurements on them. By comparing notes, users can be sure that no one else has intercepted the key, those secret keys, once established, can be used to encrypt sensitive information; By comparison, standard Internet security relies on a relatively shaky foundation of math problems that are difficult for today’s computers to solve, which could be vulnerable to the new technology, quantum computers.
But quantum communication usually has a catch, there can be no unforeseen technical problem, according to quantum physicists. For example, suppose your device is supposed to emit one photon, but unknown to you, it emits two photons. Any such failure would mean that the mathematical proof of security no longer holds and a hacker could detect the secret key, even though the transmission appears secure. Device-independent quantum key distribution can rule out such failures; the method is based on a quantum technique known as Bell’s test, which involves measurements of entangled particles. Such proofs can show that quantum mechanics really does have spooky properties, the idea that measurements of one particle can be correlated with those of a distant particle.






Responses